Kevin Mitnick Quotes & Sayings (Page 8)
Kevin Mitnick quotes and sayings page 8 (62 year old businessman). Here's quote # 71 through 80 out of the 128 we have for him.
“It doesn't work the same way everywhere. The Americans are the most gullible, because they don't like to deny co-workers' requests. People in the former Soviet bloc countries are less trusting, perhaps because of their previous experiences with their countries' secret services.”
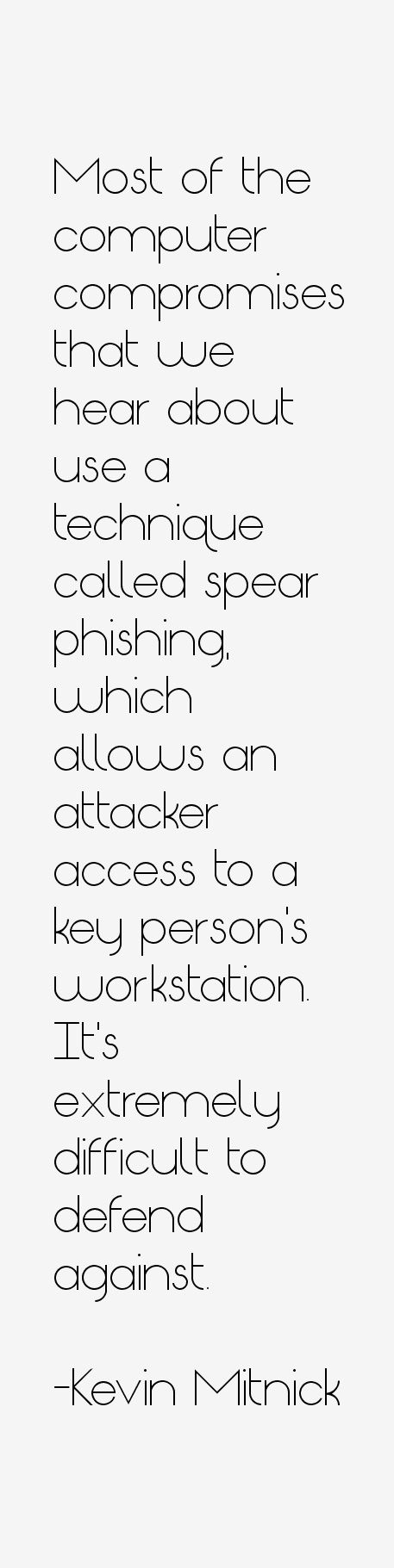
“Most of the computer compromises that we hear about use a technique called spear phishing, which allows an attacker access to a key person's workstation. It's extremely difficult to defend against.”
“One of my all-time favorite pranks was gaining unauthorized access to the telephone switch and changing the class of service of a fellow phone phreak. When he'd attempt to make a call from home, he'd get a message telling him to deposit a dime, because the telephone company switch received input that indicated he was calling from a pay phone.”
“Penetrating a company's security often starts with the bad guy obtaining some piece of information that seems so innocent, so everyday and unimportant, that most people in the organization don't see any reason why the item should be protected and restricted.”
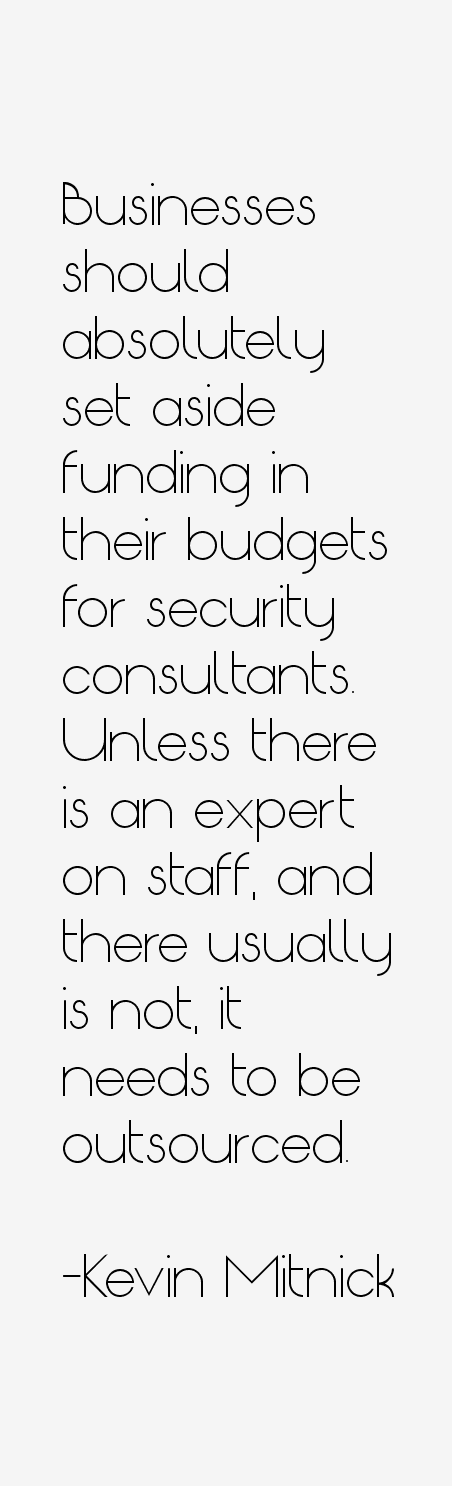
“Businesses should absolutely set aside funding in their budgets for security consultants. Unless there is an expert on staff, and there usually is not, it needs to be outsourced.”

“Most people assume that once security software is installed, they're protected. This isn't the case. It's critical that companies be proactive in thinking about security on a long-term basis.”

“So what I was essentially doing was, I compromised the confidentiality of their proprietary software to advance my agenda of becoming the best at breaking through the lock.”

“All they need to do is to set up some website somewhere selling some bogus product at twenty percent of the normal market prices and people are going to be tricked into providing their credit card numbers.”

“I trust online banking. You know why? Because if somebody hacks into my account and defrauds my credit card company, or my online bank account, guess who takes the loss? The bank, not me.”

“To have transactions made on your web site via credit card, you must be PCI compliant. Businesses make the mistake of thinking that because you passed the requirements and are PCI certified, you are immune to attacks.”
Kevin Mitnick Quotes Rating
No Ratings Yet
Leave A Comment
























